Seperating domain hosting
03 August 2024Today I took the decision that I would use separate hosting companies for the registration and name-servers of all my domains. This started out as a result of DynaDot which is the registrar I have consolidated on for almost all my domains not supporting DNSSEC but I was also not fully happy with its own name-server offerings. I had also been transferring a lot of domains recently and especially with
.com & .org domains that these days have a waiting period of a few days to allow a transfer to be vetoed, coordinating the change of registration and name-server use is a headache and I have been stung by gaps in name-server coverage.
Even in cases where registration cannot be consolidated at least administration can be, and most of the domains that I have not always switched to CloudFront's name-servers I intend to switch over to deSec's ones.
About deSEC
Stumbled across while doing search for DNSSEC providers deSEC are a German not-for-profit organisation that is focused squarely on providing free DNSSEC-enabled domain name servers. I suspect their name is in reference to the Deutschland TLD. By only providing DNSSEC-enabled DNS they have a focused interface that is intuitive to use and my plan is to use it in conjunction with my own email servers for mail forwarding — running my own DNSSEC servers is a bit much but setting up a redundant pair of VPS systems with Postfix installs is no big deal. One downside is that by default accounts only allow a single domain and I do not know how long my request for higher limits will take to be answered nor if the request will have hoops to jump though, but most likely there will be no issues and I quite like the way deSEC does one thing and does it well.About CloudFlare
CloudFlare popped up on my radar while looking for CloudFloor and the rest is history. CloudFlare is a “content delivery” network which means rather than hosting content they aid the transmission of it, with a major part of their work being dealing with the type of bottlenecks and security issues that affect high-traffic sites, but they also provide the same infrastructure to the small guys. In fact most of their customer base only use free services which is something I found out by accident after signing up. Ultimately I was after a domain name service company that supported DNSSEC and forwarding of emails and they provide both of these, with web forwarding being a bonus. The one down-side is the amount of services they offer brings with it a complicated interface that takes time to get used to.CloudFlare Web forwarding
Unlike other email forwarding systems I have seen rather than giving a wild-card there is a separate catch-all option. Press the right-hand Skip getting started and if there is a Enable Email Routing link on the next screen press it and it will give you the opportunity to add DNS MX records if any are missing. Confusingly the Routing rules tab under which the setting is found is surprisingly easy to miss when surrounded by all the other CloudFlare dashboard items. When editing the rule action can be changed to Send to an email and a destination is specified. The Destination entry widget is a bit of a pain since it is both a text entry box and a drop-down menu. If adding a new destination address a verification email is sent to it and the catch-all can only be enabled once this has been clicked through.
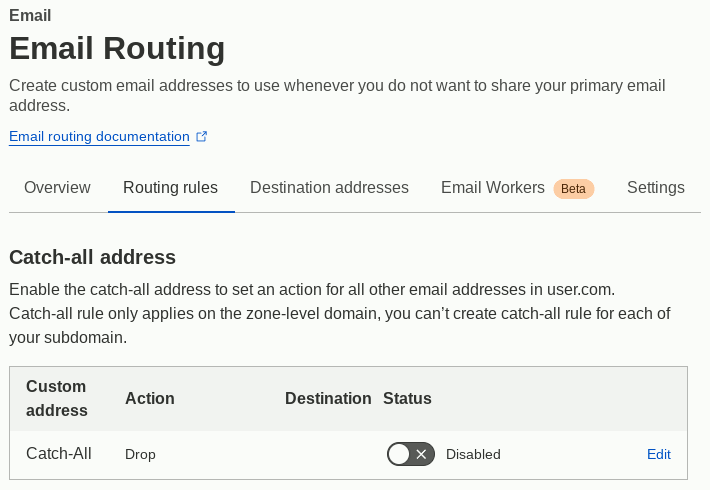
CloudFlare web forwarding
CloudFlare's way of doing redirects is more in-depth than the parking offered by registrars. Firstly the IP address specified in the DNS records have to point towards an SSL-enabled end-point rather than just any old IP address and the record has to be set to Proxied rather than DNS only for things to work. I don't know if the SSL requirement is strictly enforced or is just a warning but all things considered it best not to mess around with place-holder addresses. The actual public DNS record contains both IPv4 and IPv6 addresses of CloudFlare proxies so traffic is routed via them, and even though my end-point of my main web-server is only given as IPv4 pinging the domain name actually returned an IPv6 address.
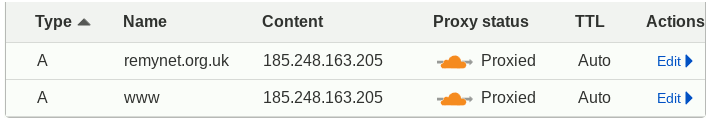
For some reason it took a lot longer for the www sub-domain to propagate than the domain root. It is while traversing their proxies that forwarding comes in and the next step is to go into Redirecy Rules under Rules which is in the lower half of the left-hand menu. It is possible to use expressions to pick out a sub-set of URLs and then there are some fancy rewriting rules, but here all that is desired is a simple forwarding of all intercepted traffic to a fixed destinaton URL. I am guessing the earlier SSL requirements is due to the need for man-in-the-middle trickery in order to filter URLs with HTTPS traffic.
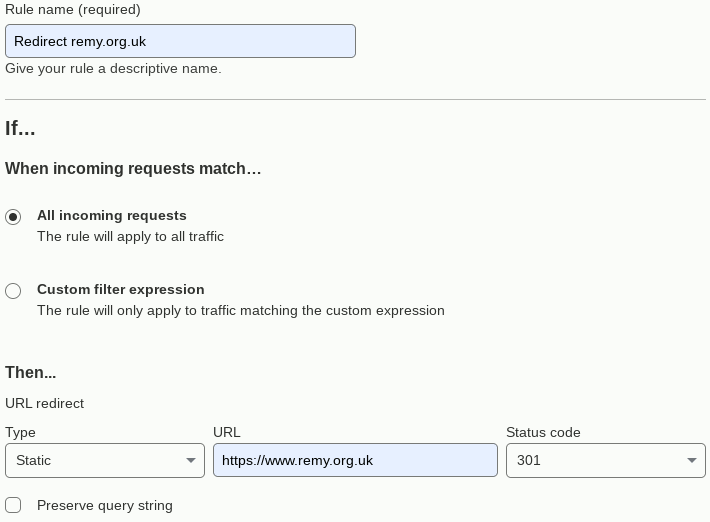
For the type Static you give just a fixed URL whereas with Dynamic you give an expession. I don't think the redirect type really matters because any traffic hitting this rule is going to be either a seriously stale link or someone typing in the address, so the distinction between temporary a permanently moved is not going to cause it to get updated automatically.